Static Application Security Testing
Source code review also known as static code analysis or static application security testing (SAST) plays a crucial role in identifying and addressing security vulnerabilities at the code level, mitigate risks early in the software development lifecycle. With the increasing complexity of applications and the advent of new technologies, the traditional way of testing may fail to detect all the security flaws present in the applications. One must understand the code of the application, external components, and configurations to have a better chance of finding the gaps. Our team does code enumeration is done line by line to identify vulnerabilities such as SQL Injection, Cross-site scripting, Business Logic Flaws, Coding practices, Unhandled exceptions, third party libraries related vulnerabilities, hard coded passwords etc. post which a detailed report is shared with customer along with recommendations. Code review helps organizations mitigate security risks by identifying and addressing vulnerabilities in the codebase. By proactively resolving these issues, organizations reduce the attack surface, minimize the potential impact of security breaches, and enhance the overall security posture of their applications.
Dynamic Application Security Testing
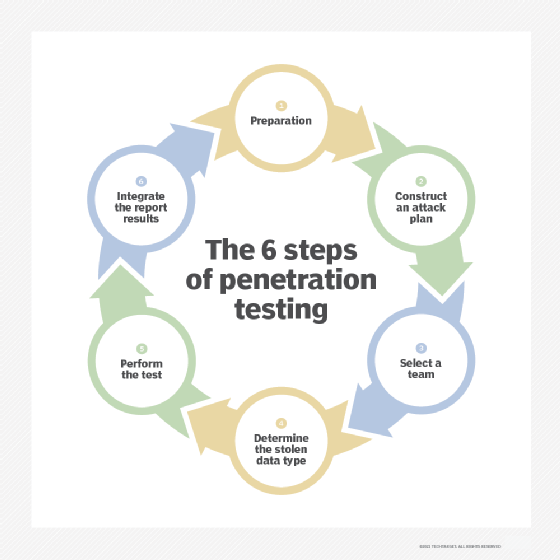
Hackers and cybercriminals are continually evolving their tactics to exploit new vulnerabilities. Regular application security testing enables organizations to stay ahead of attackers by identifying emerging threats and implementing effective security measures to counteract them. Application Security Testing is performed using industry standards such as OWASP Top 10, NIST etc. and its objective is simulating real-world attacks on an application to identify vulnerabilities and assess its resistance to exploitation. Audit is carried out manually as well as using automated tools while ensuring removal of false positives. Further, audit can be conducted either as black-box or white-box or grey-box testing as per customer need or requirement. Post testing completion, following detailed deliverables are shared with client: • Executive Summary • Comprehensive report which would include scope, objective, findings from the testing, their impact, severity, etc. • Proof-of-Concept • Recommendations along with mitigation steps and best practices Integrating security testing throughout the software development lifecycle helps in detecting vulnerabilities at an early stage. By identifying and addressing security issues during the development phase, organizations can avoid costly rework and mitigate potential risks before the application is deployed.